Open Addressing (“Closed Hashing”)
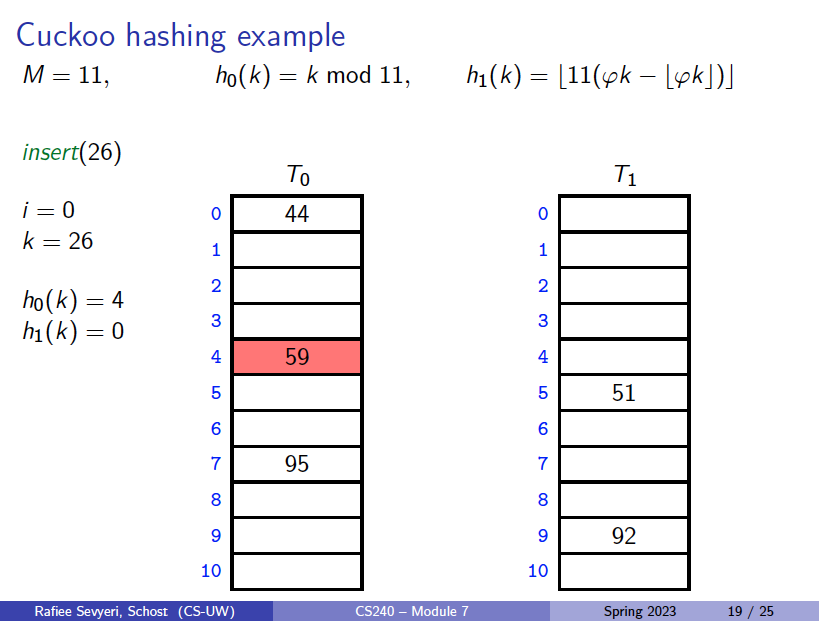
Cuckoo Hashing
This builds upon Double Hashing, where in addition to using two independent hash functions , we also use two tables .
Main idea: An item with key can only be at or .
- search and delete then take constant time.
- insert always initially puts a new item into
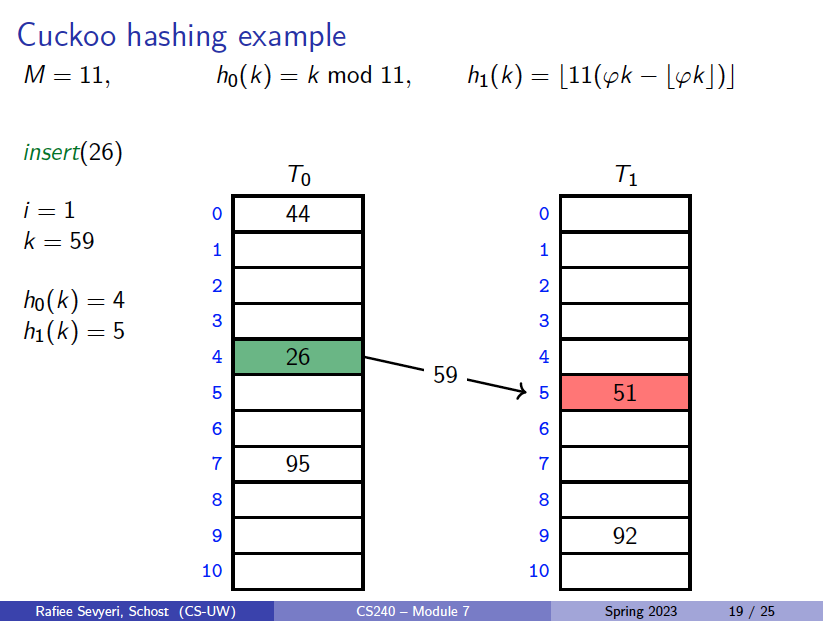
If is occupied: “kick out” the other item, which we then attempt to re-insert into its alternate position
Be careful
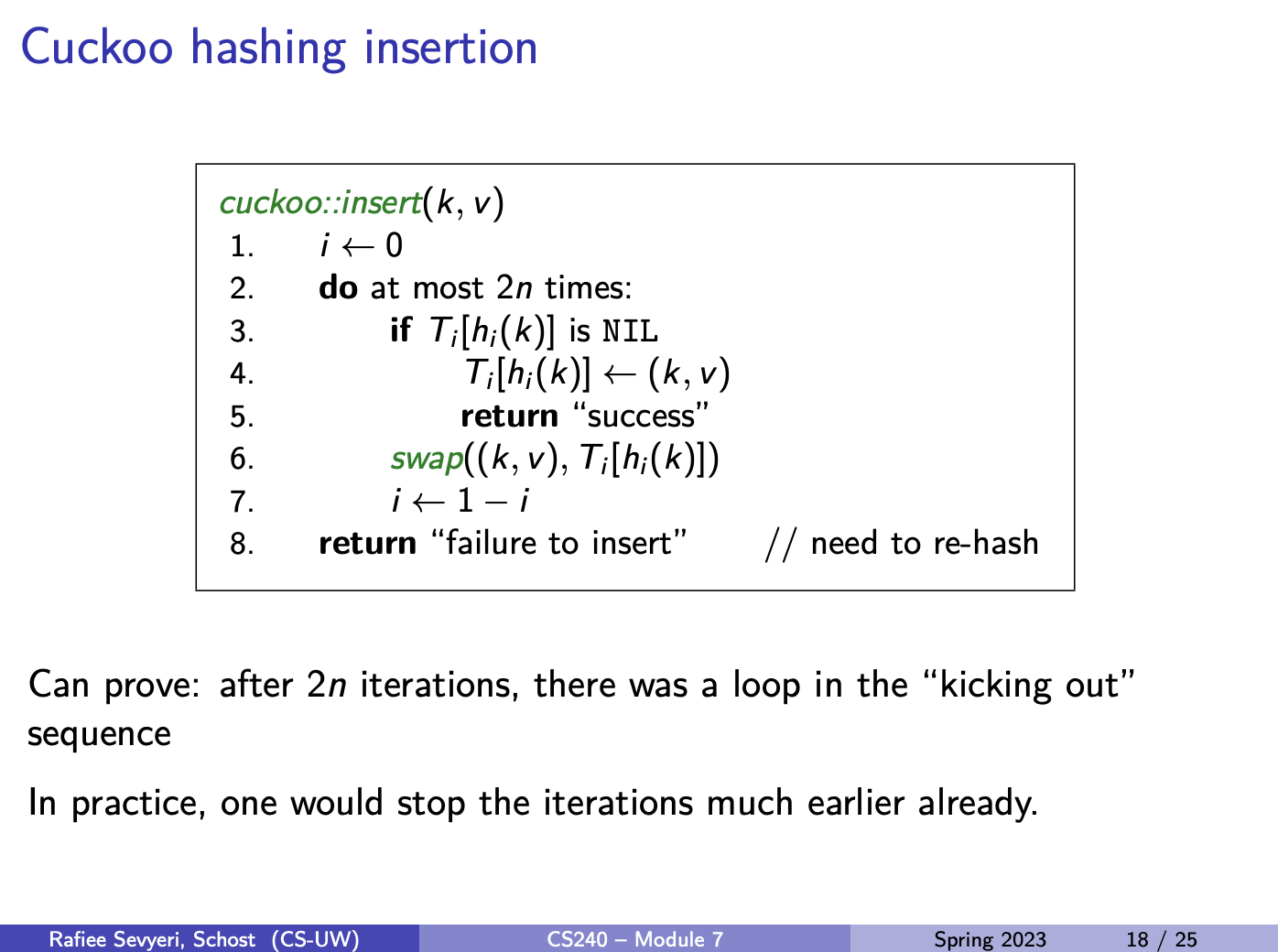
Cuckoo hashing may lead to a loop of “kicking out”. We detect this by aborting after too many attempts (doing at most times).
In case of failure: rehash with a larger and new hash functions.
For an example, see the CS240 slides.